rosehacks@pwny$ cat CSP.txt This challenge took some time to understand, but its setup is actually quite straightforward, as almost everything is provided: the payload, the Content Security Policy (CSP) header with the nonce we need to use to trigger the XSS, and even pre-captured requests. So, no actual callback server is needed. The flag is located in the admin’s cookie. The only trick here is that we need to include the nonce from the CSP in our payload; otherwise, it wouldn’t work.
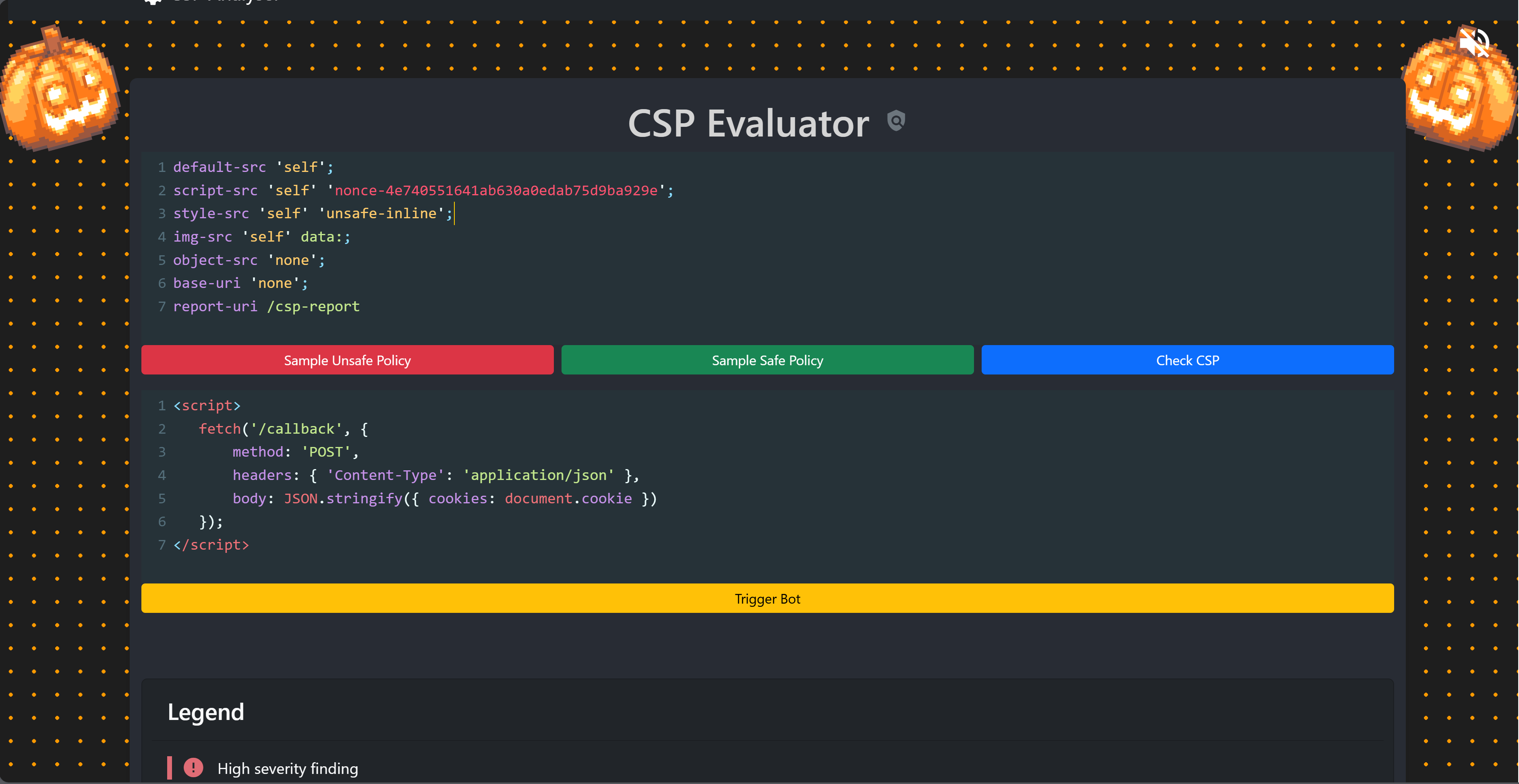
In this scenario, the CSP header is in place to restrict which scripts the browser will execute, and only those scripts with the correct nonce value are permitted. By including the nonce in our payload, we effectively “whitelist” our injected script, bypassing the CSP and allowing our XSS to execute successfully. This enabled us to capture the flag from the admin’s cookie.
The Flag
After adjusting our payload to include the nonce from the CSP, we successfully executed our XSS payload, which sent the admin’s cookie to the /callback endpoint. Checking the requests log further down the page revealed the results of our XSS payload and contained the admin’s cookie, which contained the flag.
CSP has been pwn3d!