rosehacks@pwny$ cat terrorfryer.txt In this reverse-engineering challenge, we encountered a binary executable that scrambled a given input string using an internal function, fryer. Our goal was to reverse this scrambling algorithm and retrieve the original flag.
Can you read this ?->?
Challenge Description:
The scrambled flag was given as:
1_n3}f3br9Ty{_6_rHnf01fg_14rlbtB60tuarun0c_tr1y3
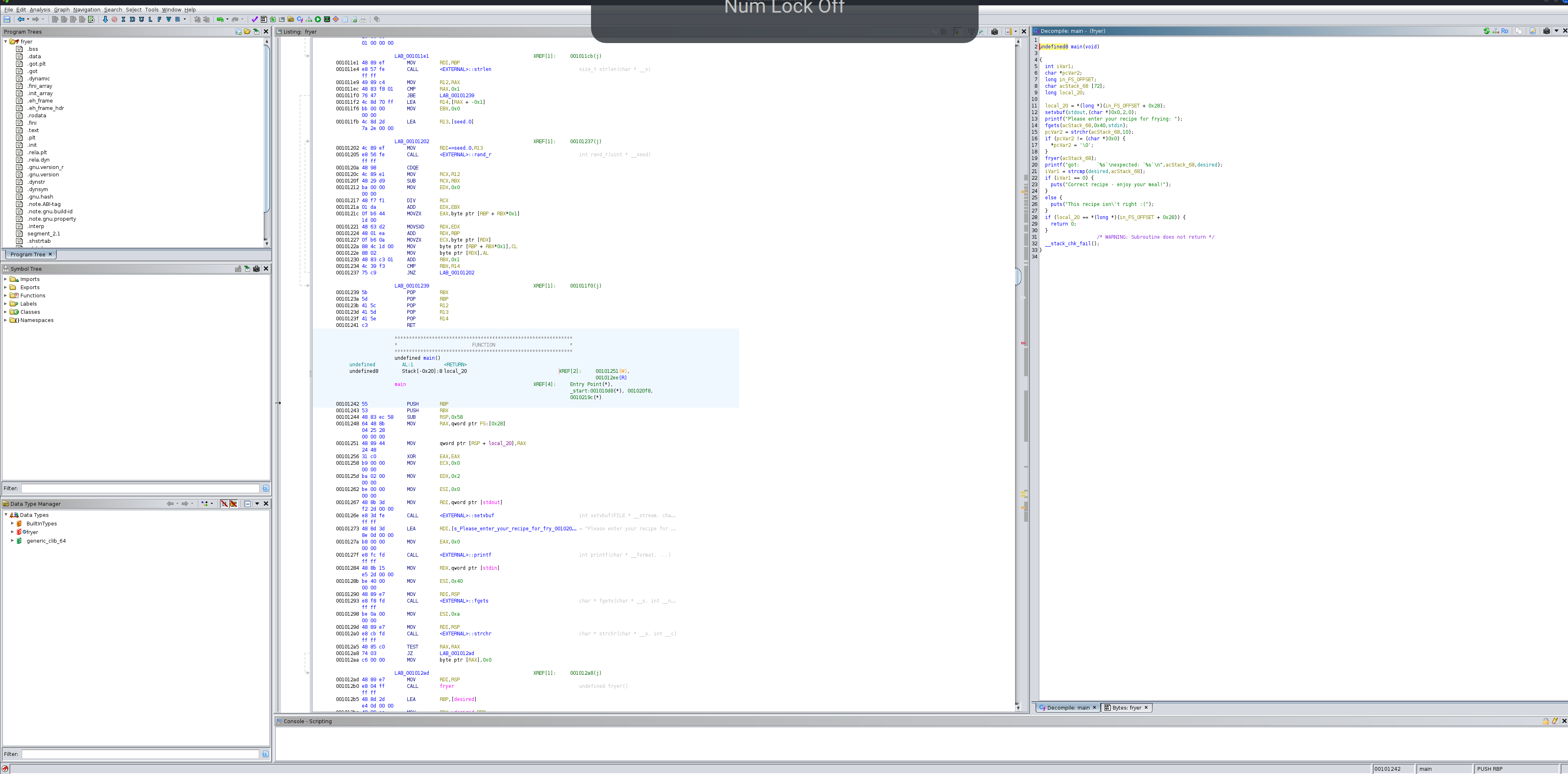
After decompiling the binary in Ghidra and looking at the available functions, it became clear that we needed to analyze the binary’s fryer function, replicate its logic, and apply the reverse operations to recover the correct flag format.
Analyzing The Fryer Function (Scrambler)
The fryer function was a scrambling algorithm written in C. It modified the input string in-place, using a sequence of swaps determined by rand_r, seeded with a static value:
void fryer(char *param_1) {
unsigned int seed = 0x13377331;
size_t length = strlen(param_1);
for (size_t i = 0; i < length - 1; i++) {
int rand_index = rand_r(&seed) % (length - i) + i;
// Swap param_1[i] and param_1[rand_index]
char temp = param_1[i];
param_1[i] = param_1[rand_index];
param_1[rand_index] = temp;
}
}
How fryer Works:
- rand_r generates a random number using the provided seed (0x13377331).
- For each character in the string, it computes a rand_index to determine which character to swap with.
- This process repeats for the entire length of the string, creating a scrambled version of the input string.
Reversing The Scramble in C
After several attempts with Python, we recognized that matching rand_r exactly was tricky. We decided to use C to replicate the scrambling and reverse it:
- Track Each Swap: During the scrambling, each swap was recorded with the exact indices that were swapped.
- Apply Swaps in Reverse: To unscramble, we simply applied each recorded swap in reverse order. By reversing each swap in this way, we effectively reversed the scramble process, recovering the original flag.
Final Solution
Our final solution was a C program that correctly implemented both the scramble and unscramble functions, relying on C’s rand_r for precise consistency:
#include
#include
#include
#define SEED 0x13377331
void scramble(char *str) {
unsigned int seed = SEED;
size_t len = strlen(str);
for (size_t i = 0; i < len - 1; i++) {
int rand_index = rand_r(&seed) % (len - i) + i;
char temp = str[i];
str[i] = str[rand_index];
str[rand_index] = temp;
}
}
void unscramble(char *str) {
unsigned int seed = SEED;
size_t len = strlen(str);
int swaps[len - 1][2];
for (size_t i = 0; i < len - 1; i++) {
int rand_index = rand_r(&seed) % (len - i) + i;
swaps[i][0] = i;
swaps[i][1] = rand_index;
}
for (int i = len - 2; i >= 0; i--) {
int index1 = swaps[i][0];
int index2 = swaps[i][1];
char temp = str[index1];
str[index1] = str[index2];
str[index2] = temp;
}
}
int main() {
char scrambled_flag[] = "1_n3}f3br9Ty{_6_rHnf01fg_14rlbtB60tuarun0c_tr1y3";
printf("Scrambled flag: %s\n", scrambled_flag);
unscramble(scrambled_flag);
printf("Unscrambled flag: %s\n", scrambled_flag);
return 0;
}</code></pre>
##### Compile and Run:
gcc -o reverse_fryer reverse_fryer.c
./reverse_fryer
This revealed the correct flag in its original, unscrambled form.
Terrorfryer has been pwn3d!