rosehacks@pwny$ cat el_mundo.txt Exploit a buffer overflow vulnerability to call the hidden function read_flag() and reveal the flag.
Initial Analysis
This binary challenge presented us with a program vulnerable to buffer overflow, where we could overwrite the return address to point to a specific function in memory. The goal was to use the overflow to redirect program execution to read_flag() and print the flag.
Solution
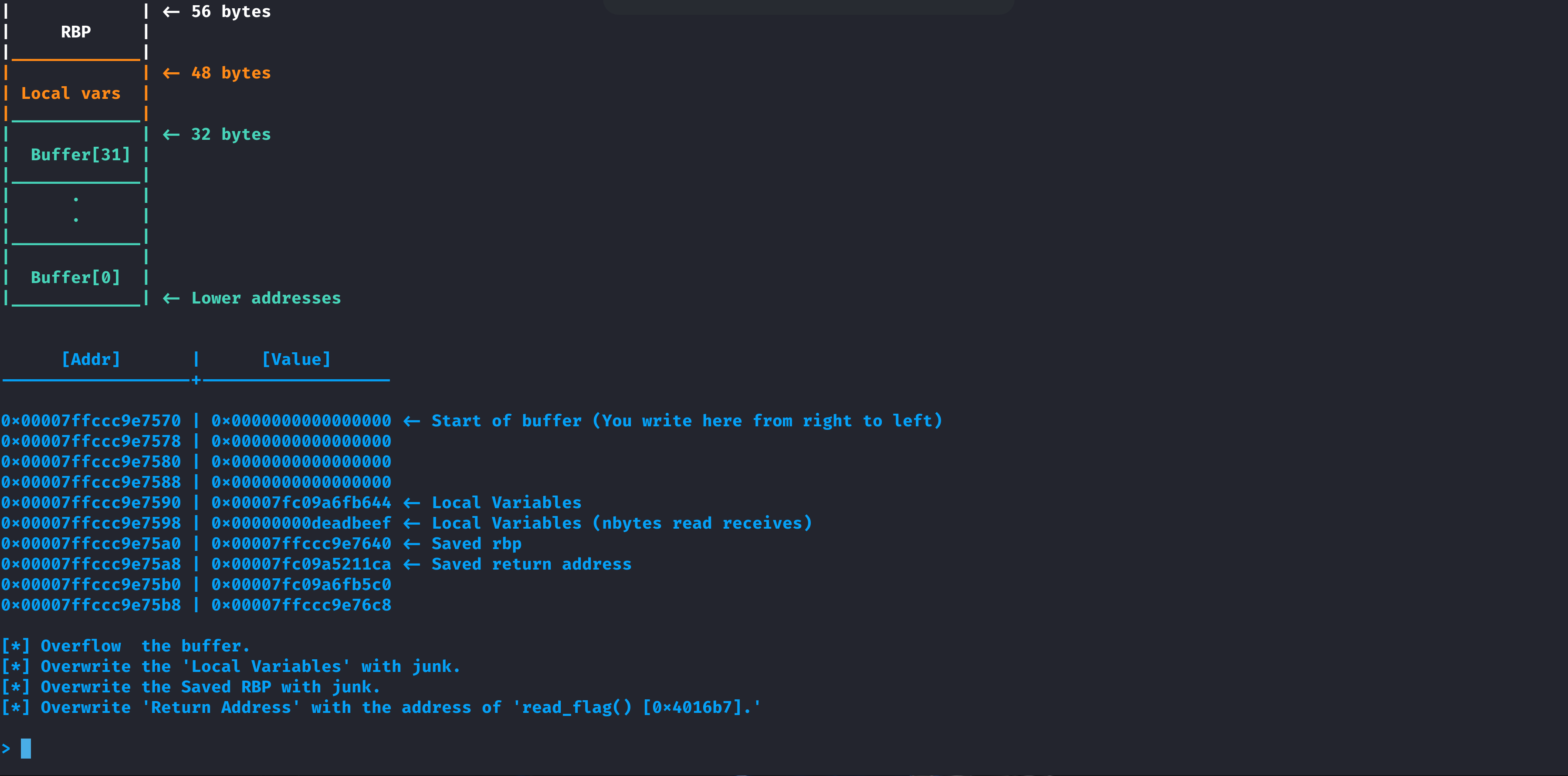
- Initial Analysis with GDB: Using gdb, I loaded the program and set a breakpoint at main() to observe the stack layout after function setup. This revealed:
- A buffer allocated at the start of the stack.
- A saved rbp address 56 bytes above the buffer start.
- A return address 8 bytes above the saved rbp.
Stack frame layout:
| Higher addresses |
| Return address | <- 64 bytes above buffer start
| Saved RBP | <- 56 bytes above buffer start
| Buffer (vulnerable) |
| Lower addresses |
-
Finding read_flag Address: The disassembled code showed that read_flag() was located at 0x4016b7. This address became our target for overwriting the return address, so we could redirect the program flow directly to read_flag().
-
Payload Construction: To craft the exploit:
- Buffer Overflow: I needed 56 bytes to reach the saved rbp, which we could fill with junk data.
- Return Address Overwrite: The next 8 bytes would hold the address of read_flag(), redirecting the execution there upon function return.
Using Python, I constructed a payload:
import struct
# Offset and address
buffer_size = 56
read_flag_address = 0x4016b7 # Address of `read_flag`
# Construct payload
payload = b"A" * buffer_size + struct.pack("<Q", read_flag_address)
# Write payload to a binary file
with open("payload.bin", "wb") as f:
f.write(payload)
- Here, struct.pack(“<Q”, read_flag_address) packed the read_flag() address as a 64-bit little-endian value, ready for injection into the stack.
- Exploiting the Program: With payload.bin created, I could redirect the program’s input to this binary file:
cat payload.bin | ./el_mundo
Running this executed the buffer overflow, overwrote the return address with read_flag()’s address, and the program executed read_flag() as intended.
- Flag Output: The program, redirected to read_flag(), printed the flag directly to the screen!
Summary
In this buffer overflow challenge, everything was pretty much given to us, which allowed us to identify and overwrite the saved return address, redirecting execution to read_flag(). This solution highlights: • Stack manipulation to overwrite return addresses. • Payload crafting with Python to inject precise binary data.