rosehacks@pwny$ cat foggy_intrusion.txt In this forensic analysis, we’re tasked with unraveling the traces of an attack that took place on some local servers. We are given a /logs directory. Inside the directory is a capture of all the event viewer logs. Our foal is to discover what the attackers have done and recover the flag.
Analyzing the Logs in Event Viewer
When conducting forensic analysis, there’s often a recommended order or priority of logs to examine. Starting with critical files can streamline the investigation and help identify the attack timeline faster. Some of the more important .evtx files to review first include:
- Security.evtx: Provides essential logs related to login attempts, privilege escalations, and any account or group changes, making it critical for tracing unauthorized access.
- Microsoft-Windows-PowerShell_Operational.evtx: This log is especially valuable if the attacker’s TTPs (Tactics, Techniques, and Procedures) include PowerShell, as it may contain specific commands they executed.
- Microsoft-Windows-Sysmon/Operational.evtx: Sysmon logs track detailed process creation, network connections, and file modifications, which can be instrumental in identifying suspicious behaviors.
- Microsoft-Windows-TaskScheduler_Operational.evtx: Task Scheduler logs help spot unusual or unauthorized tasks that may have been created to maintain persistence.
- Microsoft-Windows-TerminalServices-LocalSessionManager.evtx: Useful for tracking Remote Desktop Protocol (RDP) connections, which can reveal unauthorized access.
Extracting the flag
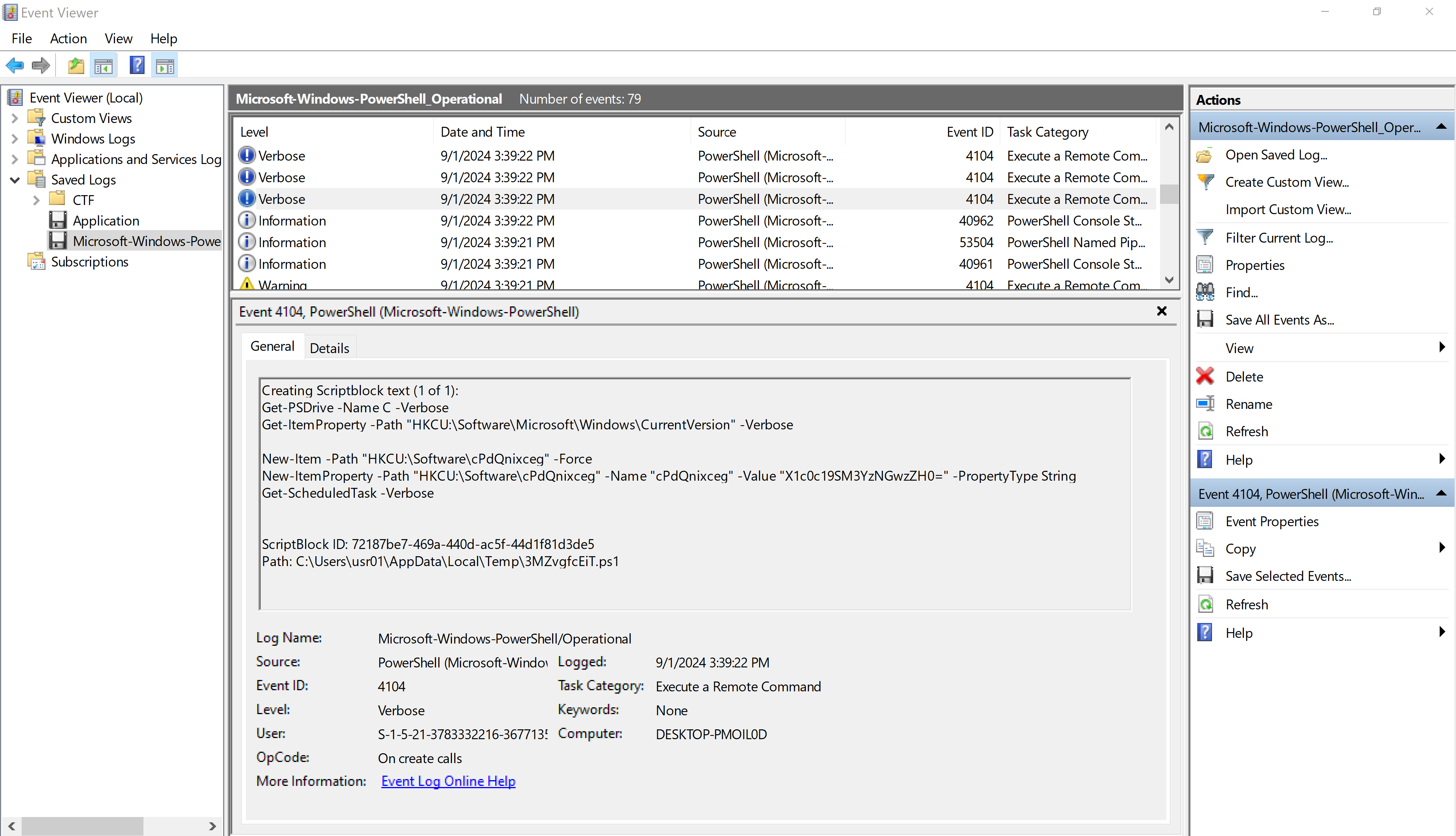
There were two parts to the flag in this challenge. Both parts were found within the PowerShell Operational logs, Which I happened to start my analysis with. Starting from the earlisted event of th log I began working my way up, looking for suspicious activities. I eventually stumbled upon an event where a PowerShell script was running a base64 encoded command. Decoding the command revealed the first part of the flag.
Part 1:
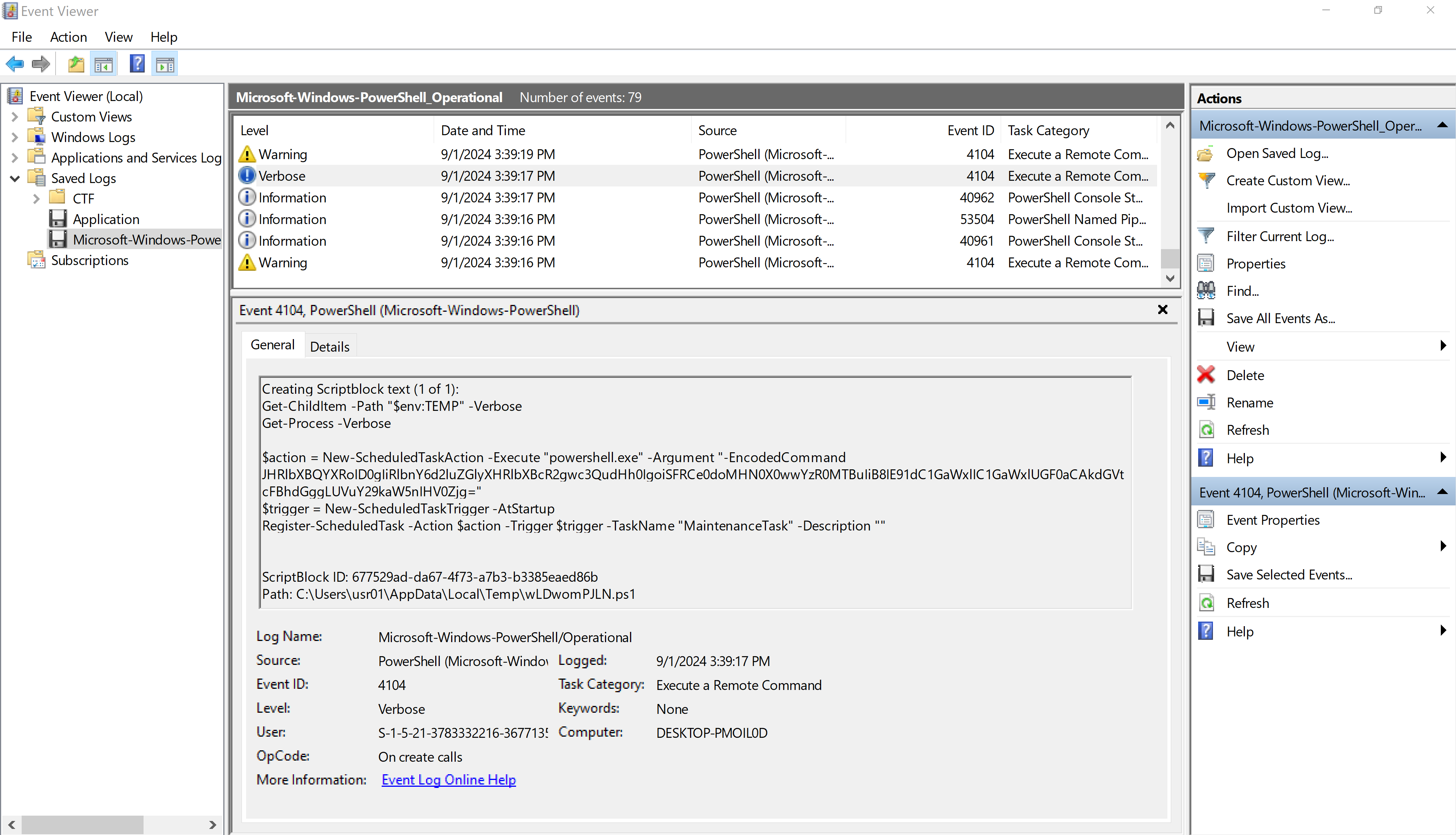
Continuing from there, I kept going through the PowerShell logs until I found another base64 encoded value in a PowerShell script. Decoding the value revealed the second part of the flag!
Part 2: