Difficulty: Easy
Description:
A popular game-selling app is secretly offering a blacklisted, highly coveted game hidden from public view. Your mission is to hack into the app’s backend, bypass its security, and uncover the hidden game to add it to your collection. Can you outsmart the system and get the forbidden game in your hands?
Challenge:
This was a very easy web challenge. The application uses the username value in the JWT to determine when the flag renders on the index page. It renders the page differently depending on the username inside the JWT. So, I was able to forge a JWT for any user, in this case the “admin” user, and retrieve the flag.
Vulnerable Code:
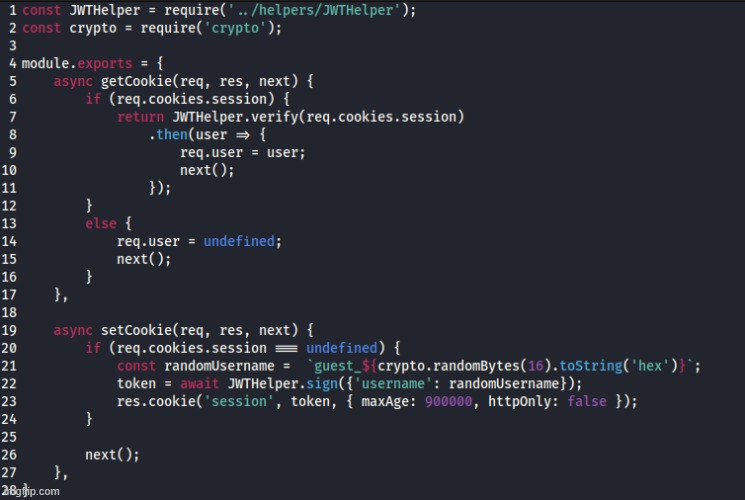
Inside the AuthMiddleWare file there are two functions, the setcookie and the getcookie function. The getcookie function checks if the incoming request has a cookie, if not the setcookie function generates one with a randomly generated username, such as “guest_ewiufhu4h98hf”. It then signs the cookie.
AuthMiddleWare.js file:
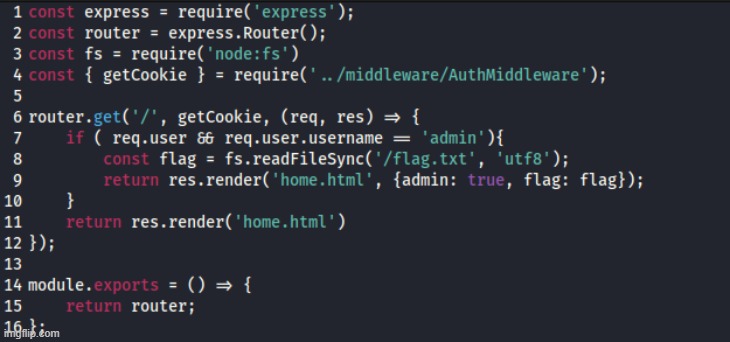
The routes file gets the cookie from the AuthMiddleWare and checks the value of the “username”, if it is equal to admin it reads the flag from /flag.txt and renders it on the index.html page, if the value is anything else, it just loads the index.html page without the flag.
Routes.js file:
Solution:
After landing on the application, we notice there isn’t much in terms of functionality. Just a static page. So, with that, one of the first things I checked, was the esistence of a cookie using the developer tools. An sure enough there was a JWT sitting in my storage.
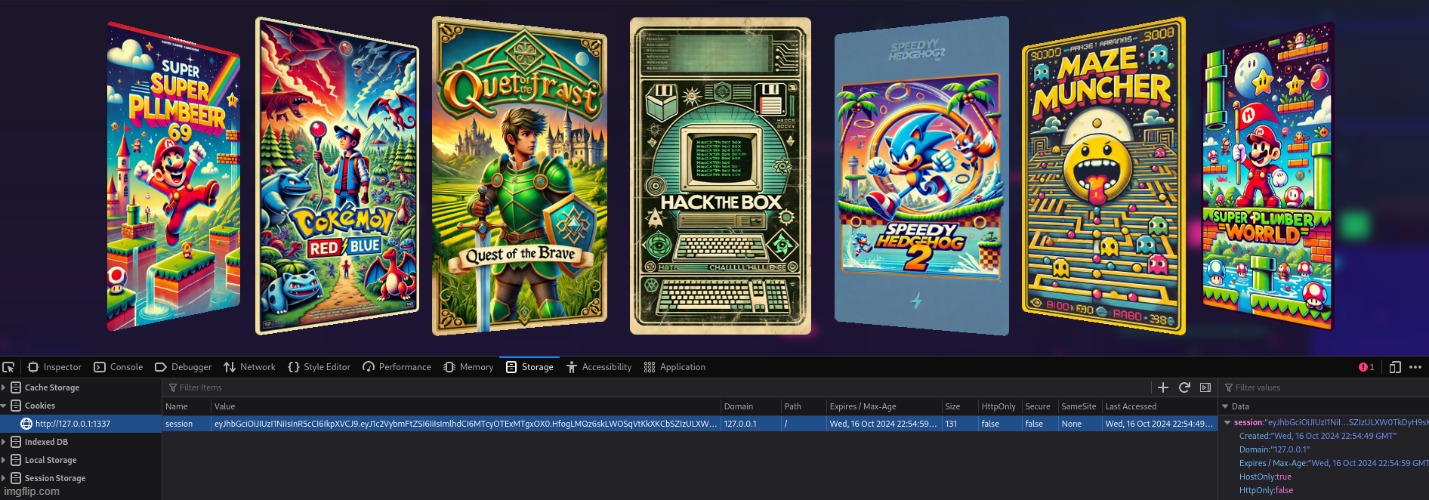
I copied the JWT and pasted it into JWT.io (a JWT debugger) to analyze it. The username is defined in the cookie. I tried changing mine from guest_088u98u3498u89 to “admin” to see if the application would render the home page differently.
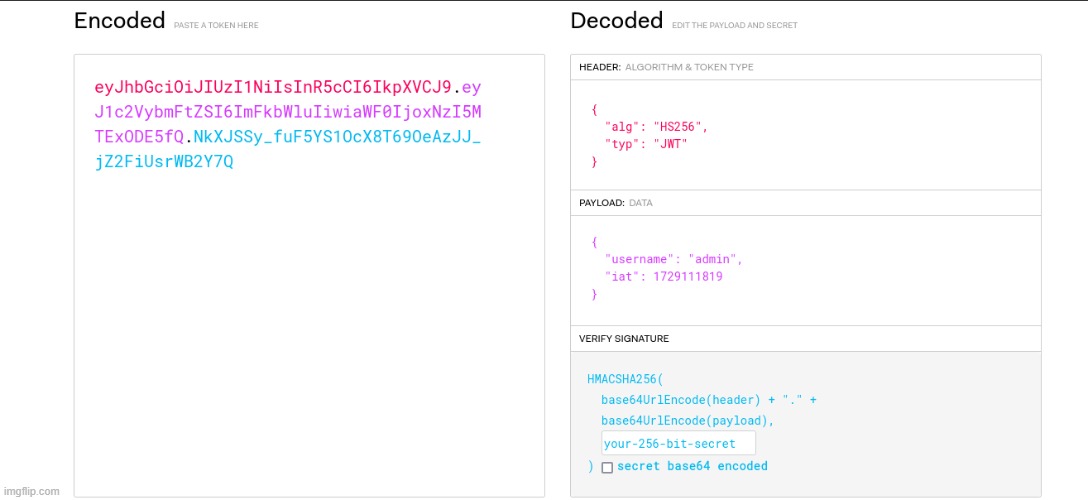
After copying the newly forged JWT, I pasted it into the storage and refreshed the page: